ATLAS: could save you from an almost inevitable cyber attack by performing regular Vulnerability Scans and providing easy-to-follow remediation instructions.
CLOSING THE DOORS TO HACKERS
The complexities surrounding today’s computers and networks require regular “vulnerability” scanning and remediation to detect and defend against the evolving threats from hackers who use holes in these systems to create a potentially devastating effect on your business.
Constant changes to devices, configurations, applications and even new patches can leave you susceptible to an attack, even if you are keeping your security controls up to date.
IS THE THREAT REAL?
- A new security vulnerability is identified every 90 minutes.
- There are an average of 7 vulnerabilities per asset across a typical IT environment.
- 8000 new vulnerabilities are identified each year, many of these are categorised as critical.
- It takes an average of 103 days until known security vulnerabilities are remediated.
- It takes an average of just 15 days for a new vulnerability to be exploited.
Being information Security specialists enables us to provide cyber-security products and services to help protect your business against these very real threats.
“Gartner considers vulnerability assessment a foundational component of a greater information and security management program.”
Gartner Market Guide for Vulnerability Assessment
ATLAS: VULNERABILITY ASSESSMENT
WHAT IS IT?
![]() Vulnerability Assessment Scanning is the technical inspection of a computer or network to identify security holes (“vulnerabilities”) that an attacker can exploit to cause major disruption to your business or steal sensitive information. A vulnerability scan detects and classifies these weaknesses allowing early remediation.
Vulnerability Assessment Scanning is the technical inspection of a computer or network to identify security holes (“vulnerabilities”) that an attacker can exploit to cause major disruption to your business or steal sensitive information. A vulnerability scan detects and classifies these weaknesses allowing early remediation.
WHY YOU MUST CARE ABOUT IT
![]() You can’t fix what you don’t know about so if your computers and networks have “vulnerabilities” you are making the job of a malicious hacker much easier who may use these weaknesses to steal sensitive information or cause major disruption to your business. Many of these security holes are an open door for hackers but can be easily mitigated with help from our detailed automated reports and comprehensive, easy to follow, remediation documentation.
You can’t fix what you don’t know about so if your computers and networks have “vulnerabilities” you are making the job of a malicious hacker much easier who may use these weaknesses to steal sensitive information or cause major disruption to your business. Many of these security holes are an open door for hackers but can be easily mitigated with help from our detailed automated reports and comprehensive, easy to follow, remediation documentation.
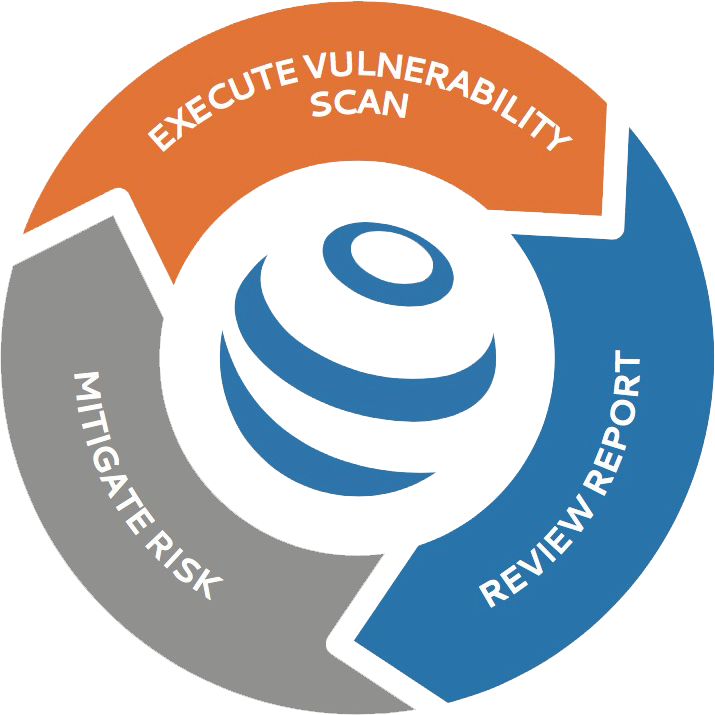
HOW DOES IT WORK?
![]() Our Vulnerability Assessment Scans are simple to operate and fully automated so you won’t need any technical knowledge to start the process. All detected weaknesses are available to view on our highly secure user-friendly portal along with easy-to-follow instructions on how to remediate any issues found. If you use a third-party IT company, this information can simply be handed to them for any remediation work to be completed.
Our Vulnerability Assessment Scans are simple to operate and fully automated so you won’t need any technical knowledge to start the process. All detected weaknesses are available to view on our highly secure user-friendly portal along with easy-to-follow instructions on how to remediate any issues found. If you use a third-party IT company, this information can simply be handed to them for any remediation work to be completed.
WHY IS THIS DIFFERENT TO ANTI-MALWARE WE HAVE INSTALLED?
![]() Installing anti-virus/malware software is a critical part of your overall Information Security strategy but you can no longer rely solely on this for protection because many of today’s sophisticated attacks can circumvent these applications. You must routinely perform vulnerability scans of all connected devices and remediate where necessary to give you the best chance of mitigating an almost inevitable attack.
Installing anti-virus/malware software is a critical part of your overall Information Security strategy but you can no longer rely solely on this for protection because many of today’s sophisticated attacks can circumvent these applications. You must routinely perform vulnerability scans of all connected devices and remediate where necessary to give you the best chance of mitigating an almost inevitable attack.